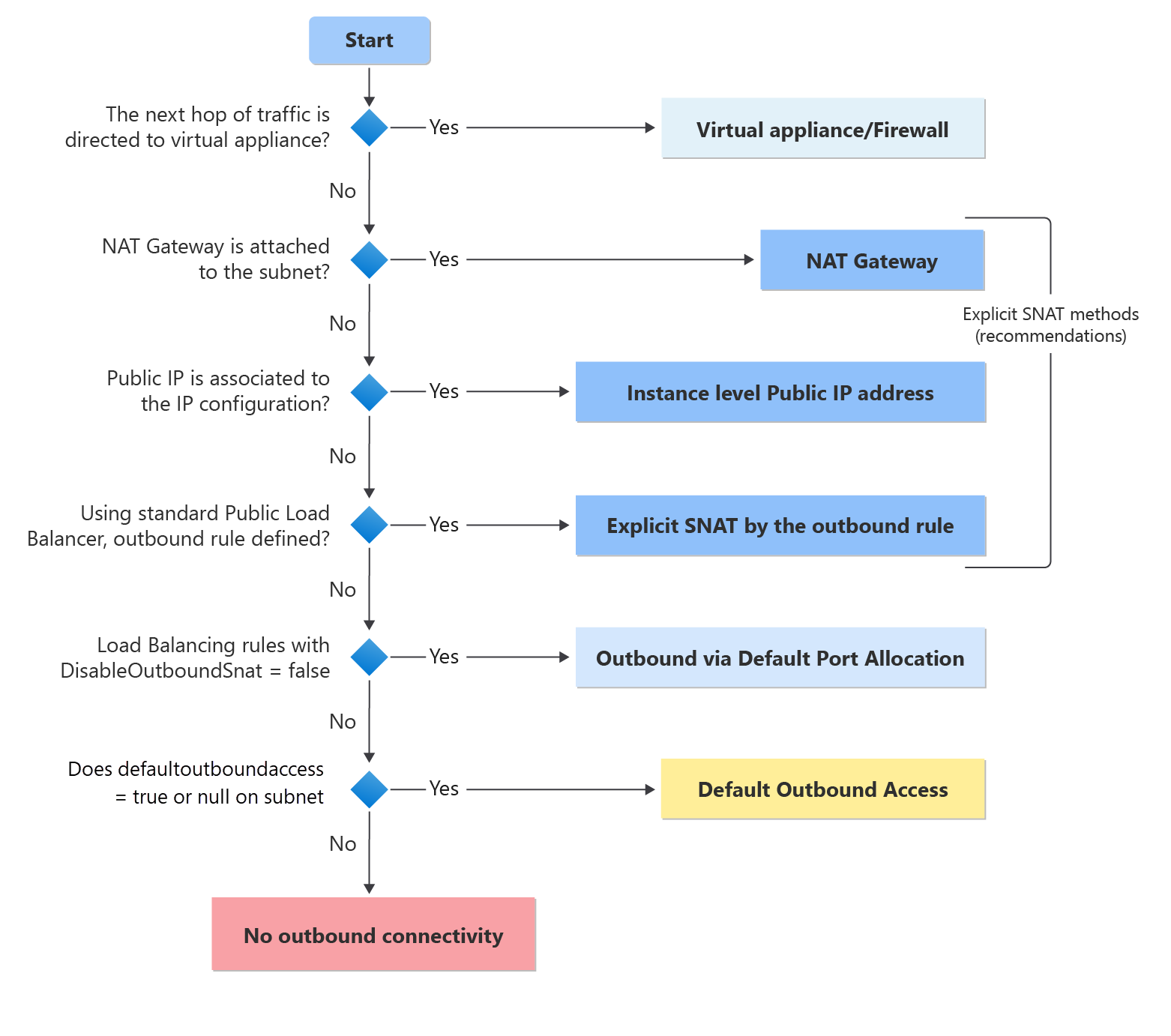
Network Security Groups (NSGs) are a critical component of Azure’s security model, enabling you to control network traffic to and from your resources. By defining rules that allow or deny specific traffic, NSGs help protect your cloud infrastructure from unauthorized access and potential threats.
Why NSGs are essential for cloud security
In a cloud environment, security is paramount. NSGs act as a virtual firewall, allowing you to define granular rules for inbound and outbound traffic at both the subnet and network interface levels. This flexibility ensures that only authorized traffic reaches your resources, reducing the attack surface and enhancing overall security.
NSGs are a foundational security feature in Azure, and every cloud architect should understand how to use them effectively.
Key features of NSGs
Rule-based traffic control: NSGs allow you to create rules based on source and destination IP addresses, ports, and protocols. This is known as a five-tuple rule.
| Attribute | Description |
|---|---|
| Source | 🌐 The IP address or range of addresses from which the traffic originates. |
| Destination | 🎯 The IP address or range of addresses to which the traffic is directed. |
| Protocol | 🔗 The protocol used (e.g., TCP, UDP, or ICMP). |
| Port | 🚪 The port number or range of ports involved in the communication. |
| Action | ✅/❌ The action to take (Allow or Deny) |
These five elements form the foundation of NSG rules, enabling precise control over network traffic.
Priority-based evaluation: Rules are evaluated in order of priority, with the lowest number taking precedence.
Default rules: Azure provides default rules to ensure basic security, such as denying all inbound traffic unless explicitly allowed.
Logging and monitoring: NSGs integrate with Azure Monitor to provide insights into traffic patterns and rule effectiveness.
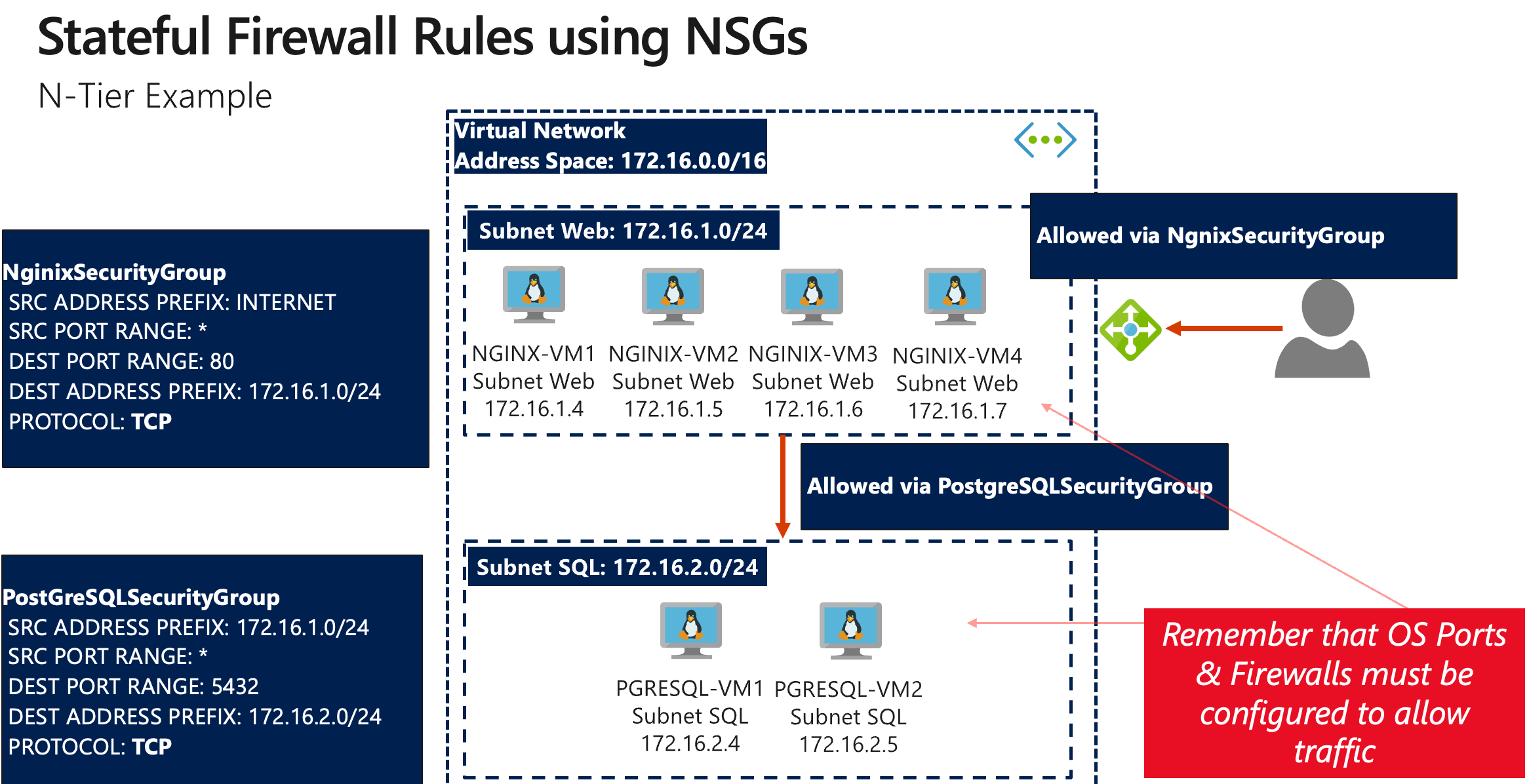 Diagram illustrating how NSGs filter traffic at the subnet and NIC levels.
Diagram illustrating how NSGs filter traffic at the subnet and NIC levels.
Best practices for configuring NSGs
- Use least privilege: Only allow the traffic that is absolutely necessary for your application to function.
- Separate environments: Use different NSGs for development, testing, and production environments to avoid accidental exposure.
- Monitor and audit: Regularly review NSG rules and logs to ensure compliance with security policies.
- Combine with other tools: Use NSGs alongside Azure Firewall and Application Gateway for a layered security approach.
“Security is not a one-time setup; it’s an ongoing process of monitoring, adapting, and improving.”
Common use cases for NSGs
- Web applications: Restrict inbound traffic to specific ports (e.g., 80 and 443) while blocking all other traffic.
- Database servers: Allow traffic only from specific application servers or subnets.
- Virtual machines: Limit RDP or SSH access to trusted IP ranges.
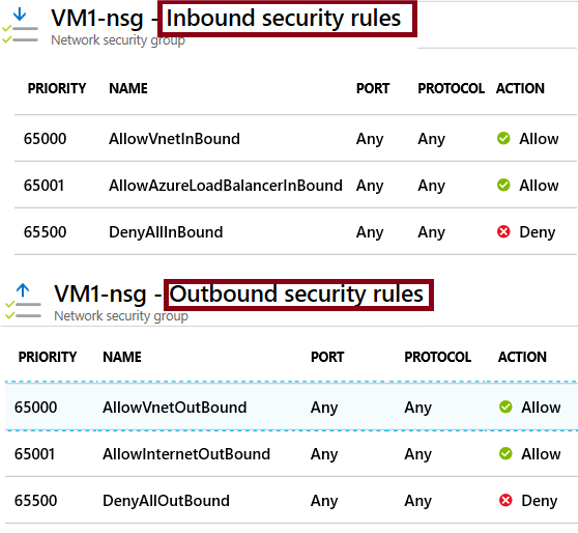 Diagram illustrating how NSGs filter traffic at the subnet and NIC levels.
Diagram illustrating how NSGs filter traffic at the subnet and NIC levels.
How to create and manage NSGs in Azure
- Create an NSG: Use the Azure portal, CLI, or PowerShell to create a new NSG.
- Define rules: Add inbound and outbound rules based on your security requirements.
- Associate with resources: Apply the NSG to a subnet or network interface.
- Test and validate: Use tools like Azure Network Watcher to verify that your rules are working as expected.
Always test your NSG configurations in a non-production environment before applying them to critical resources.
// Example: Automating NSG creation with Azure CLI
az network nsg create --resource-group MyResourceGroup --name MyNSG
az network nsg rule create --resource-group MyResourceGroup --nsg-name MyNSG \
--name AllowHTTP --priority 100 --direction Inbound --access Allow \
--protocol Tcp --source-address-prefix '*' --source-port-range '*' \
--destination-address-prefix '*' --destination-port-range 80
By leveraging NSGs effectively, you can significantly enhance the security of your Azure environment. Whether you’re managing a small application or a large-scale enterprise deployment, NSGs provide the flexibility and control needed to protect your resources.